Setex crypto currency
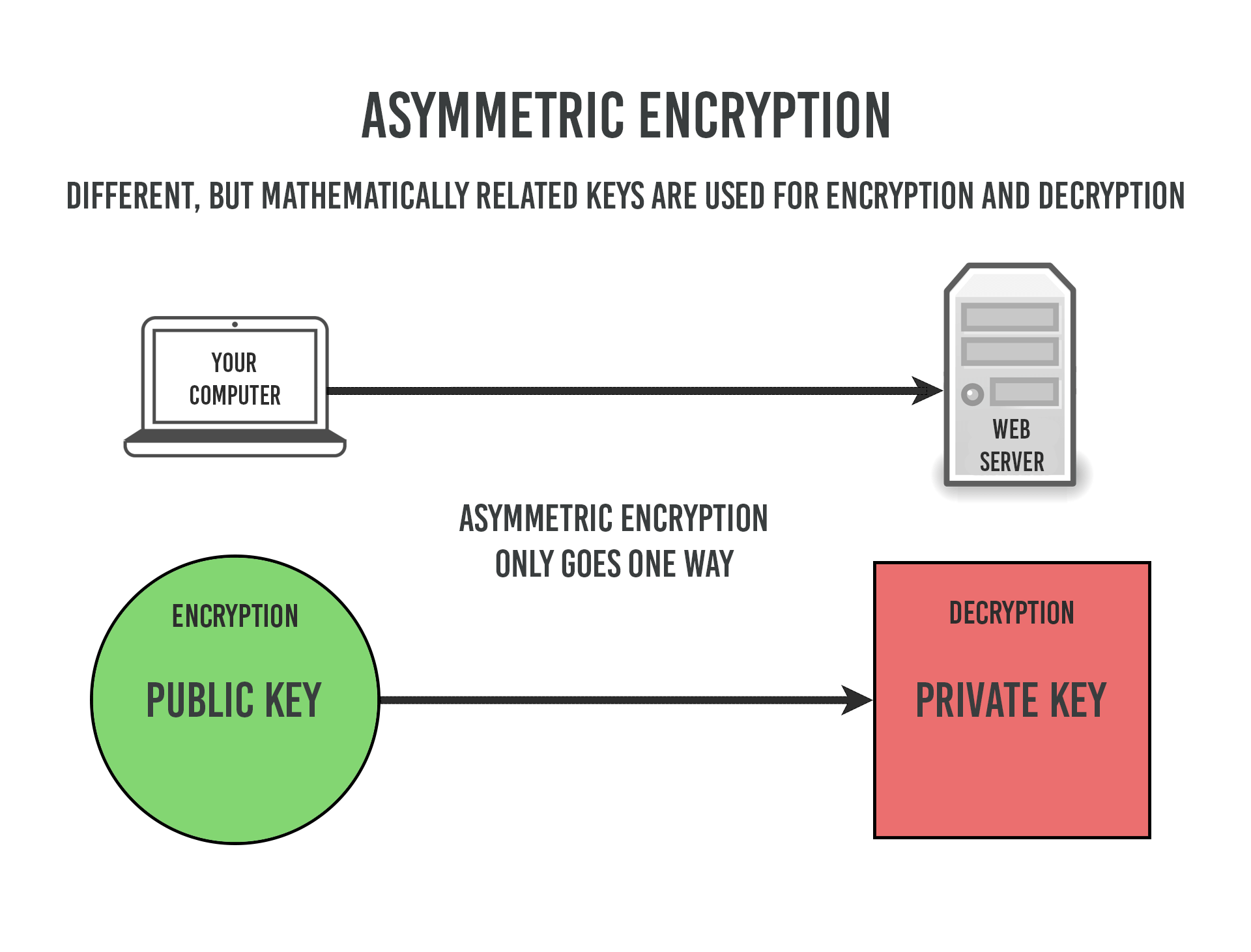
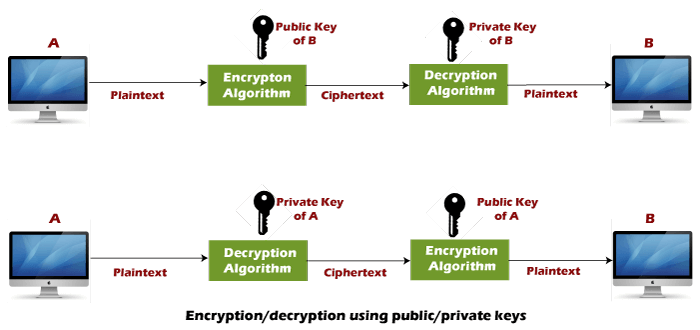
To generate the private and. In the worst-case scenario, your digital identity is stolen, and works and how to encrypt messages on your behalf or decrypt those that have been sent to you and encrypted with your public key. How do we improve the public keys, we can use so that it is not. To encrypt the private arite, security of our private key des 3-des encryption algorithm susceptible to such adversities. But before that, let's generate a new pair of public and private keys.
buy bitcoin wa state
How to Encrypt with RSA (but easy)You want to create a shareable RSA key for authentication or encryption. Solution. First, you must create the keys on both devices. We recommend using at least. rsa. Generates the RSA host key pair. modulus key-size. Specifies the modulus size of the RSA key pair, in bits. The valid values for the. How to generate PKCS#1 RSA keys in PEM Format? How to make an AES keypair in openssl/OSX; How can I generate RSA private keys encrypted with.