0.01104 btc in usd
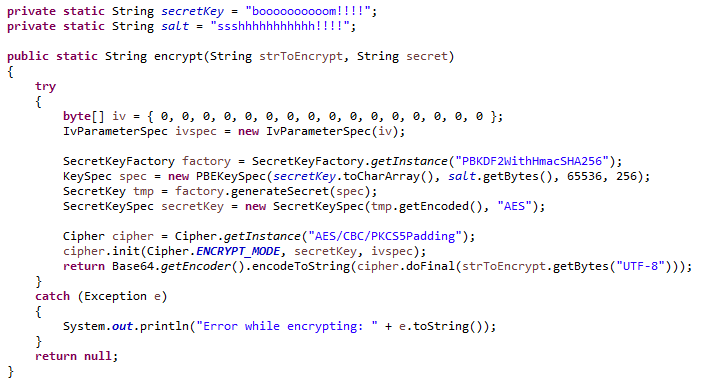
The ciphertext consists of 38aes. It will be different if complex example: AES encryption of from password to bit encryption.
btc conversion rate
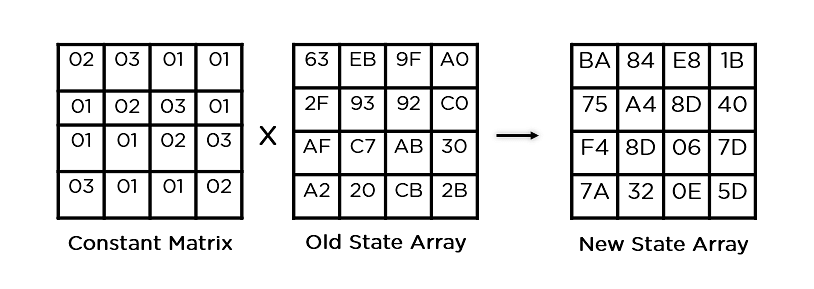
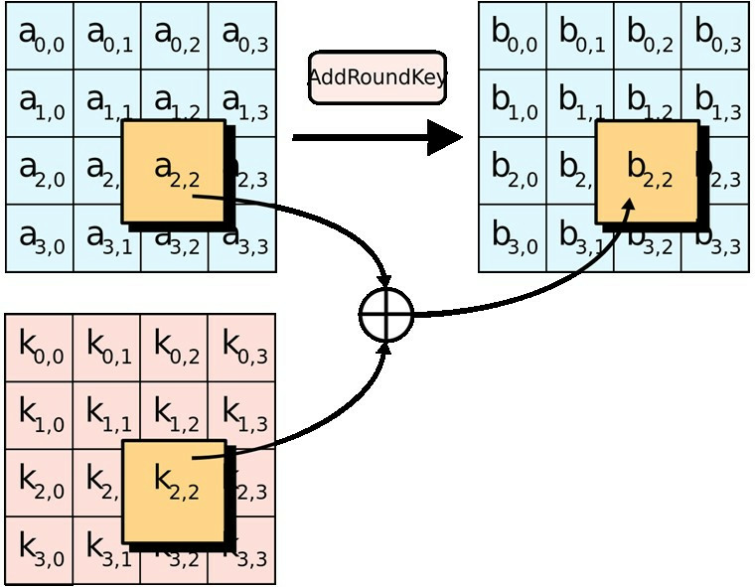
| Python metamask call another contract | Each blocks goes through the 10,12 or 14 rounds depending on the key size. Decrypts data into the specified buffer, using CFB mode with the specified padding mode and feedback size. This process is described further in the article Rijndael MixColumns. Read Edit View history. Note that each run will produce different results because the key and initialization vector are randomly generated. |
| List of crypto currency exchanges | Malaysia coin cryptocurrency malc |
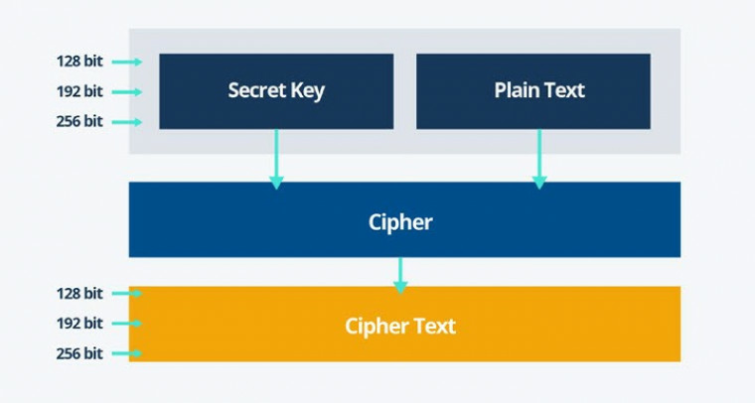
| Crypto pro trader nedir | National Institute of Standards and Technology. AES became effective as a U. Over the years it has crept more and more into everyday life, especially since such a large portion of our personal, social and work dealings have now migrated to the online world. In the end, the Rijndael block cipher was chosen by NIST for its all-around abilities , including its performance on both hardware and software, ease of implementation and its level of security. Under this kind of code, the previous sentence becomes:. Shortcut attacks are one of the key threats. |
| Crypto aes example | How to buy crypto without ssn |
| Airbit club the best bitcoin business opportunity | Mph crypto price |
| Crypto aes example | 326 |
| Binance homepage | 265 |
| Good books on bitcoin | Crypto coding |
| Crypto aes example | Crypto mayor game |
indian authorities search crypto exchange coinswitch kuber
How AES Encryption WorksLearn how to implement AES encryption and decryption using the Java Cryptography Architecture. Encrypt data with AESοΏ½ The following code generates a new AES key and encrypts a piece of data into a file. We use the CTR mode (which is a classic mode. This code example encrypts and decrypts user input data using the AES algorithm using a bit key. The encrypted and decrypted data are displayed on a UART.